This blog is now archived
This blog is now archived
Please note that this blog is no longer being updated.
Please note that this blog is no longer being updated.

In this post we discuss jailbreaking and why organisations may want to detect and prevent it from happening on their devices. Administrators and risk owners should take note of what risks jailbreak detection actually mitigates, and what risks are left …
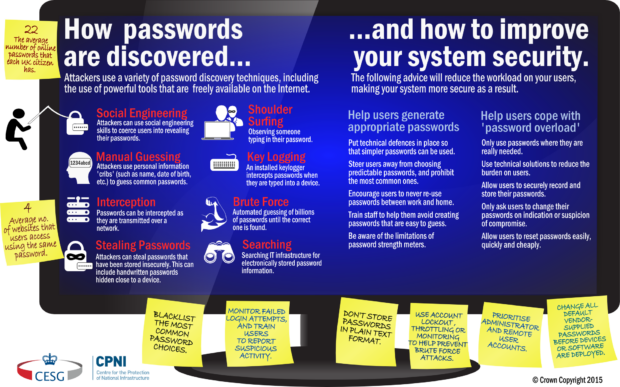
Start talking with users about security and pretty quickly you end up on the topic of passwords. Passwords are probably the security measure that everyone runs into on a daily basis. We have passwords for our IT systems at work, …

It's been a while since I last blogged about the new Online Services team. There's a lot to report, so this will be the first of a short series of blogs giving an update on progress. This first blog post …
If you were at the joint SIRO, CTO and DSO Event at Church House in London last week on Digital Transformation and Security, you will have heard Ciaran Martin announce that CESG has stood up a new online services team. …
Back in November 2014, we published an alpha set of principles on “Risk management of cyber security in technology projects”. You may have noticed that we recently issued a beta version following analysis of feedback and some further testing

The CESG Digital team is working to propose an alternative approach for making sensible security decisions that relate to OFFICIAL technology.

A few weeks ago, CESG began using the approach set out in the Service Design Manual to help develop our services.
Recent Comments